Application penetration test sql
If this is the case, a malicious user could provide unexpected inputs to the application that are then used to frame and execute SQL statements on the database. Therefore if not being validated, such input can also return any unexpected result and inform the same, that this attack is possible in this case.
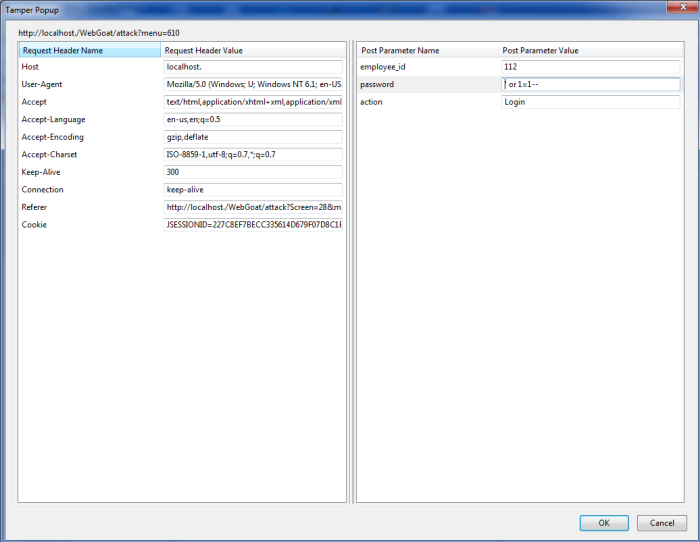



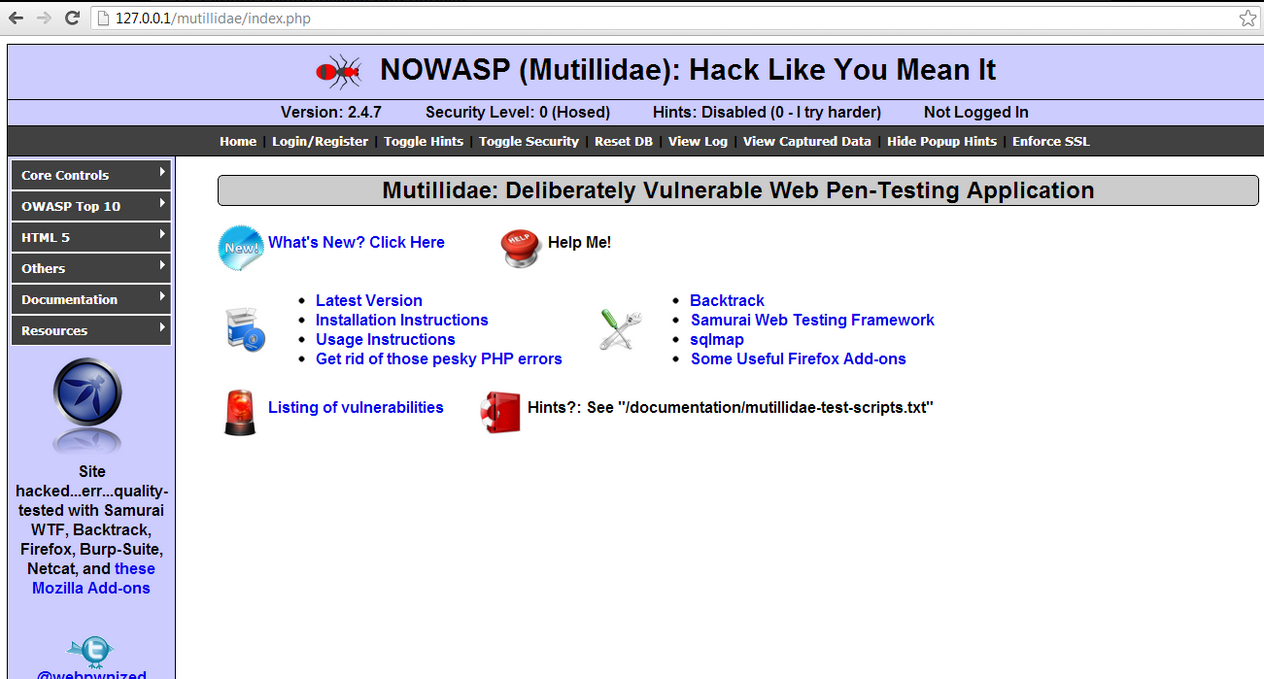


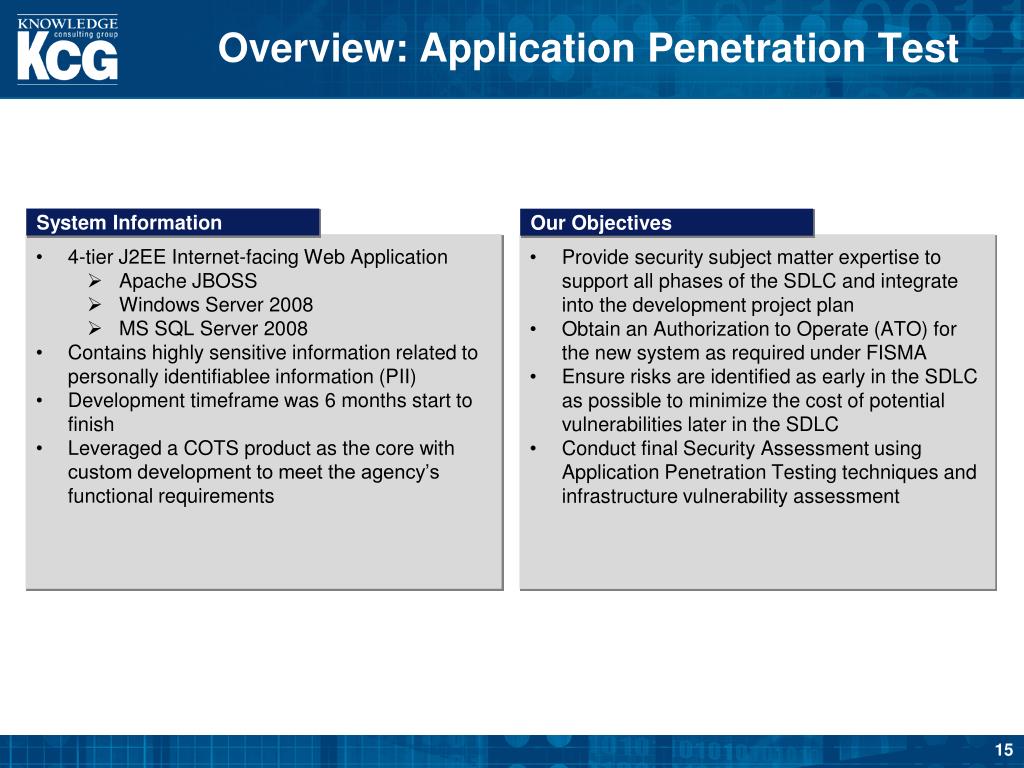
Common SQL Injection Attacks
You may need it to check target in different geographies, simulate nonpersonalized browsing behavior, anonymized file transfers, etc. To emphasize the difference between an application and a web application, penetration testing the web application mainly focuses on the environment and the setup of the web app.
Carter Cruise is playing with her sweetness little vagina at pieceofwork when her interviewee comes inwards. She figures atpresent that she has a existent life guy inward her businessoffice he tin take attention of her needs. As a bonus, if he gets her to comeup the task is his.
Web Application Penetration Testing: Steps, Methods, & Tools
Have you come across any typical SQL Injection?

Description: Double penetration of my wife. Mobile phone market penetration. Enemas and anal penetration stories.


























 Charlotte. Age: 21
Charlotte. Age: 21

User Comments 3
Post a comment
Comment: